A Guide to Proactive Anti-Ransomware Strategy
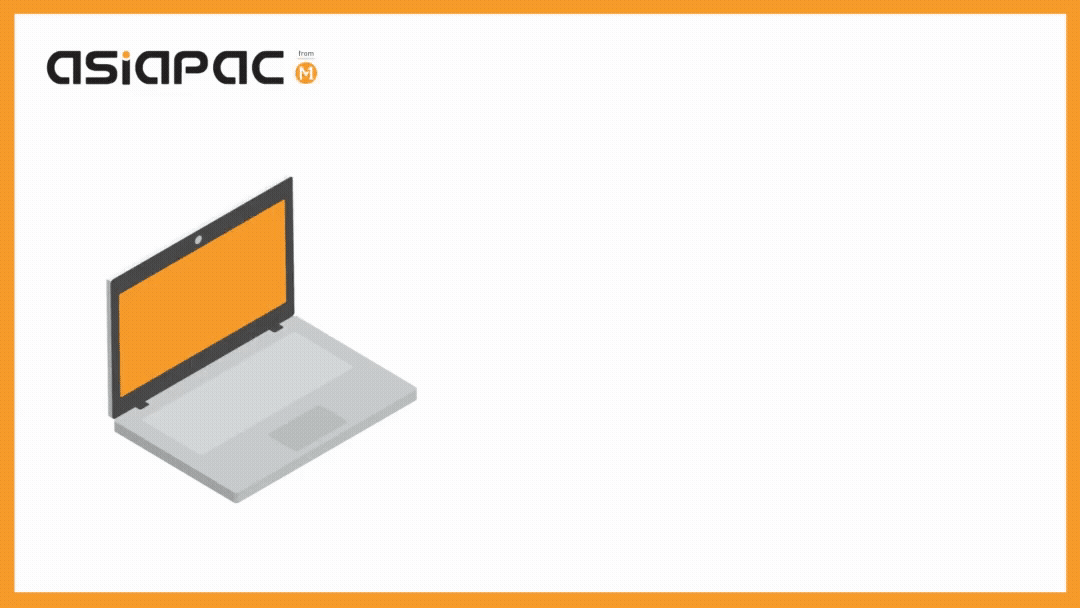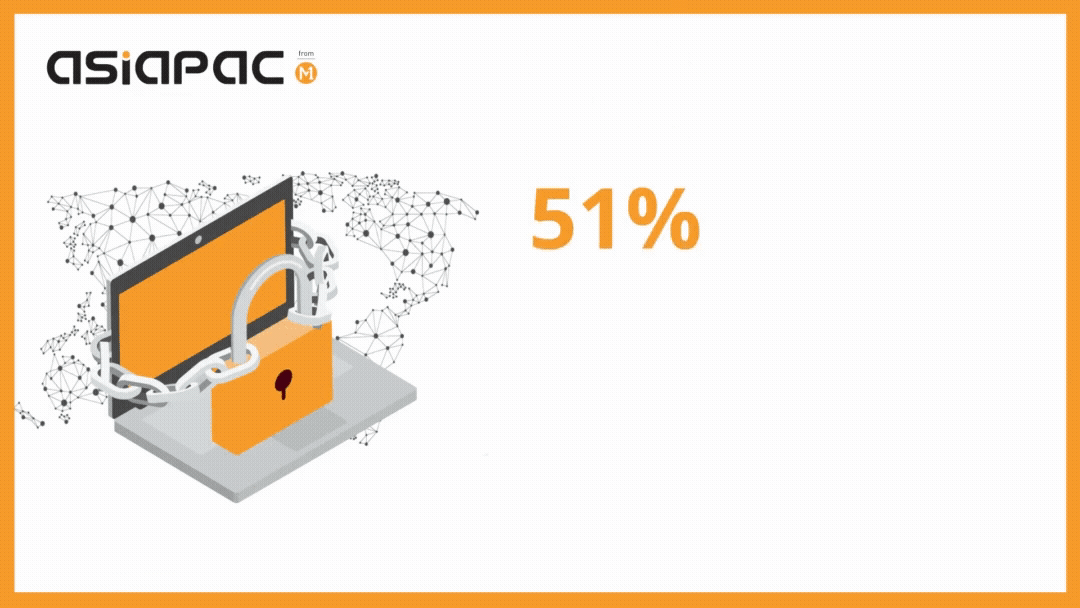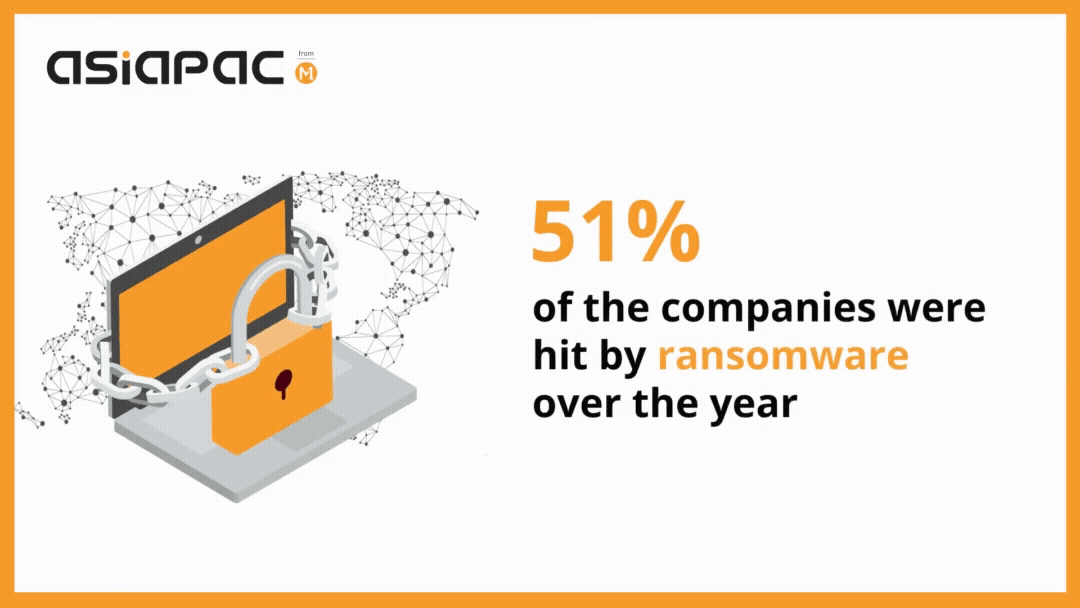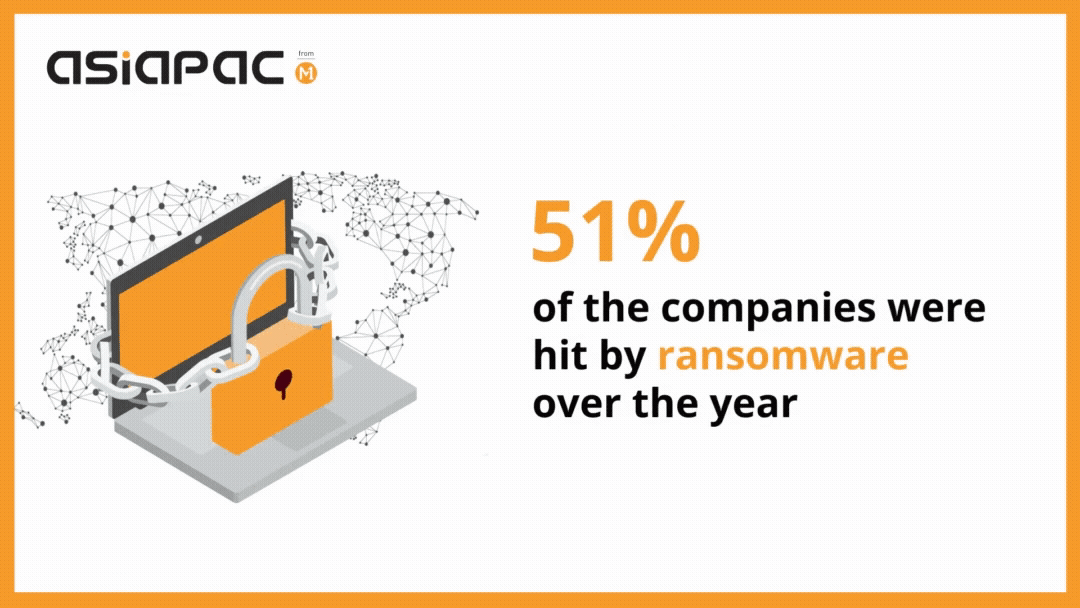
As per a recent survey, the average ransom demand from businesses hit by ransomware attacks was $178,000 in 2020. The same survey revealed that 51% of the surveyed companies were hit by ransomware over the year.
These numbers, although disconcerting, are not surprising in the least. There has been an uptick in ransomware attacks in the recent years, and they are becoming more common and more sophisticated with time. The fact that ransomware attackers typically demand ransom in bitcoins or other difficult-to-trace cryptocurrencies only makes it harder for law enforcement officials to catch the perpetrators. Naturally, more and more cybercriminals are adding ransomware to their arsenal.
This brings us to the big question – What can businesses do to protect themselves against the rising incidences of ransomware attacks?
To answer this question, it’s vital that businesses understand what ransomware is and how it works.
How Ransomware Works?
Ransomware is a type of malware that uses sensitive information of individuals and businesses to hold them hostage for a ransom.
There are primarily 2 types of ransomware. The first kind collects sensitive information about a person or business and threatens them to publish that information unless they make a ransom payment. The second kind encrypts “important” data and makes it inaccessible to the owner, who must now pay a ransom to regain access to their data.
The most common delivery method of ransomware malware is a phishing email. An authentic-looking email containing the malware is sent to unsuspecting recipients. The malware could be hidden within the email as a link or an attachment (invoice, image, etc.). Once the recipient opens the infected email and downloads the malware, it invades their computer and connected systems surreptitiously. Once it has encrypted all the critical data, it throws up the ransom notification to the user.
Sometimes, the attackers may use fake pages of trusted businesses (banks, cloud providers, etc.) to obtain login credentials from the users to plant the malware. Alternatively, they can even use brute-force methods, although rarely, to enter corporate systems.
How to Protect Your Organization From Ransomware Attacks in 6 Steps
The most effective way to prevent ransomware attacks is through vigilance. There is no single tool or workaround to prevent ransomware attacks in their entirety. A combination of vigilance, rigorous safety measures, and awareness of the threats is required to fight the menace. Here is a 6-step strategy to bolster your security posture against ransomware attacks:
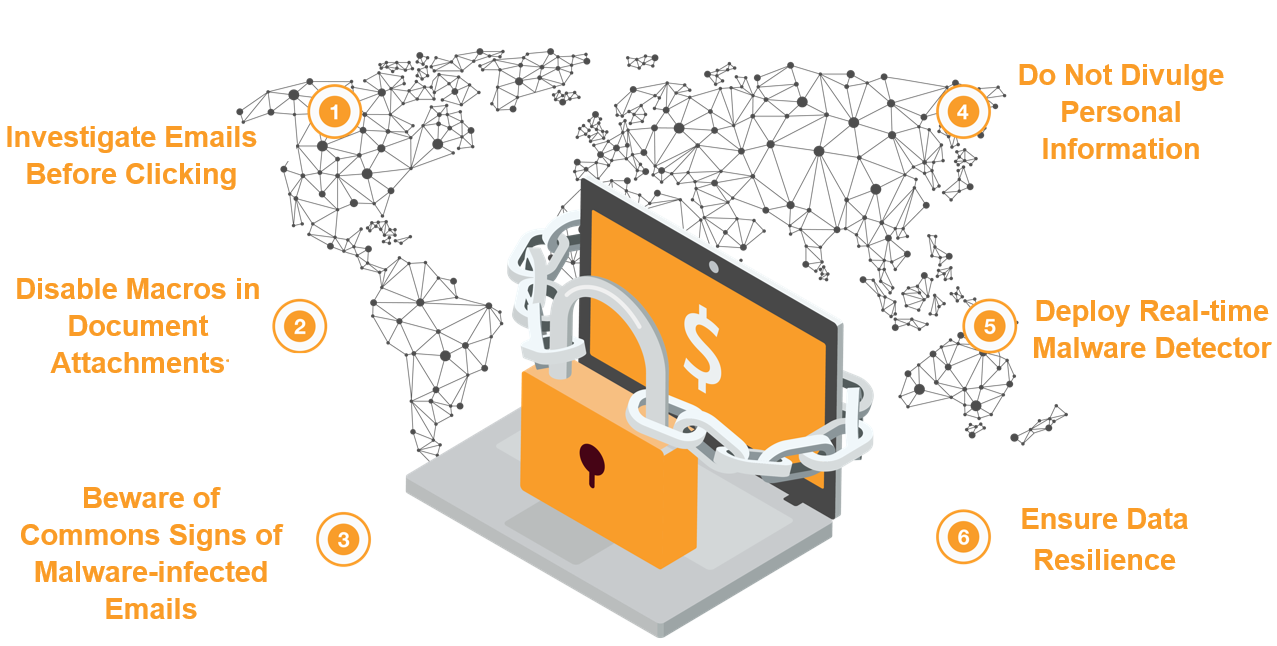
1. Investigate Emails Before Clicking
Ransomware attackers often disguise their emails as legitimate communication from reputed sources. Therefore, look for signs of suspicious activity. If you do not know the sender or have no reason to receive any mails from them, then do not open the emails. When you do open them, check the sender’s email address to ascertain its authenticity.
Also, do not display the images in the email. Instead, hover the mouse cursor over the links in the email. If any of the links reveal suspicious addresses, then mark the email as spam. Do not click on anything in the email body unless you are 100% sure that it’s legitimate. Even when the email sender looks genuine, if you have other reasons, no matter how remote, to believe that something is fishy, do not open the email.
2. Disable Macros in Document Attachments
Microsoft® deliberately turned off auto-execution of macros by default as a security measure. Many infections rely on persuading you to turn macros back on, so please never do it, especially if these messages are via emails.
3. Beware of Commons Signs of Malware-infected Emails
Infected emails are often riddled with spelling errors. Businesses, especially large corporations and financial institutions, are extremely cautious about the language they use in their communications. Common spelling errors, formatting errors, and poor grammar are clear signs of an infected email.
Another telltale sign of an infected email is a pushy subject line. Threatening language, fear-mongering messages, or urgency-inducing subject lines are designed to invoke emotional responses and get recipients to download the malware unwittingly.
4. Do Not Divulge Personal Information
Legitimate companies and financial institutions will never ask for personal credentials via email or through a phone call, even more so from consumers protected by PDPA. Never divulge your personal information remotely. You are not obliged to do so. If you must, then visit the organization’s office.
5. Deploy Real-time Malware Detector
Commercially available anti-malware software protection solutions are the first line of defense against attacks by known and identified ransomware. Although they offer no protection against emerging ransomware threats, they are highly effective against the identified threats.
Some of the more robust solutions feature artificial intelligence capabilities that can help you against even the most sophisticated attacks. Ransomware attackers have evolved from a ragtag band of operators into well-funded and highly resourceful organized syndicates, which consistently improve their malware. AI-powered software protection solutions can identify patterns in their behavior and detect such advanced threats that may elude human experts.
6. Ensure Data Resilience
It’s impossible to ensure complete protection from ransomware attacks. Therefore, it’s vital to have a Plan B, Plan C, Plan D, and so on. Take regular backups of your critical data. Automate the backups when possible. Take additional steps to ensure fast recovery and business continuity in the case of breaches.
Conclusion
Ransomware attacks are growing in intensity and complexity. Awareness, vigilance, and a proactive anti-ransomware strategy together can keep your organization’s sensitive data safe and secure from such attacks.
AsiaPac’s team of security specialists bring with them the tools, the technologies, and the expertise required to bolster your organization’s security posture against ransomware attacks. We can also educate your employees in identifying malware-infected emails, and improve your vigilance against such threats. Get in touch with us to learn more.
Tags: AsiaPac Managed Services, backup, Cyber threats, Cybersecurity, Data Breach, Data Security, Managed Services, Ransomware, remote workforce, Security, SMBs, Startups,
Other blog posts you might be interested in:
Trending posts
- AsiaPac | Automation Anywhere ‘Best Performance Partner of the Year 2021’ Award
- AsiaPac is now an Authorized Apple Reseller in Singapore
- AWS ASEAN Partner of the Year Award 2022 – Singapore
- Hitachi APAC Data Center Modernization Partner Contest Award
- Migrating to Cloud? Secure Your Hybrid Cloud with Trend Micro
- AsiaPac Technology awarded the Microsoft Singapore Intelligent Cloud – Azure Partner of the Year Awards 2023

