Why Intelligent Privilege Control is Crucial for Identity Security?

In today’s digital age, identity security has become a major concern for individuals and organizations alike. It’s not just about protecting sensitive data, but also ensuring that only authorized users have access to it. One of the key components of identity security is privilege control, which refers to the process of granting or denying access to specific resources based on the user’s role and responsibilities. However, simply controlling access is not enough. With the increasing sophistication of cyber threats, it’s crucial to have intelligent privilege control in place. This involves leveraging advanced analytics and machine learning algorithms to identify and respond to suspicious activity in real-time. In this article, we will explore why intelligent privilege control is so critical for identity security, and what steps you can take to implement it in your organization. So, let’s dive in and learn more about this essential aspect of digital security.
Understanding Intelligent Privilege Control
Intelligent privilege control is a next-generation approach to privilege management that goes beyond the traditional role-based access control (RBAC) model. It leverages machine learning algorithms and advanced analytics to identify and respond to suspicious activity in real-time. By analyzing user behavior patterns, intelligent privilege control can detect potential security threats and take action to prevent them. This approach provides a more proactive and dynamic way of managing privileges, as it can adapt to changing circumstances and respond to new threats as they emerge.
The Importance of Identity Security
Identity security is critical for individuals and organizations alike. It’s not just about protecting sensitive data, but also ensuring the privacy and safety of users. When identities are compromised, it can have serious consequences, including financial loss, reputational damage, and legal liabilities. Identity theft is one of the fastest-growing crimes in the world, with millions of people falling victim to it every year. In addition, cyber threats are becoming increasingly sophisticated, making it harder to detect and prevent them. As a result, it’s more important than ever to have robust identity security measures in place.
Common Identity Security Threats
There are many different types of identity security threats that organizations need to be aware of. These include phishing attacks, ransomware, malware, social engineering, and insider threats. Phishing attacks are one of the most common types of security threats. They involve tricking users into providing their login credentials or other sensitive information through fake emails or websites. Ransomware is another serious threat, as it can lock users out of their own systems and demand payment in exchange for access. Malware can also be a significant threat, as it can infect systems and steal sensitive data. Social engineering involves tricking users into revealing sensitive information through psychological manipulation. Finally, insider threats can be especially dangerous, as they involve trusted employees or contractors who have access to sensitive data.
The Role of Intelligent Privilege Controls
Any identity can become privileged based on the sensitive resources they can access — and the actions they can take. Consider the example of a healthcare system, where a wide range of identities (human and non-human) requires protection, including:
- IT admin identities with high-risk access to critical healthcare infrastructure.
- Identities of everyday hospital employees, 65% of whom have access to sensitive data such as patient records and billing information.
- Identities of automated tools used by the hospital’s DevOps team to build out cloud operations as healthcare modernizes.
- Built-in identities on endpoints and servers that an attacker could use to steal patient data or install ransomware that could shut down hospital operations.
- Machine identities built into healthcare Internet of Things (IoT) devices used by medical staff and patients.
Healthcare is just one example. This phenomenon — in which identities of all types are gaining access to critical resources, infrastructure and environments — is happening across all industries and government sectors.
Intelligent Privilege Control vs. Traditional Privilege Control
Intelligent privilege control provides a more proactive and dynamic approach to privilege management. It leverages machine learning algorithms and advanced analytics to analyze user behavior patterns and detect potential security threats. By identifying anomalous activity, intelligent privilege control can take action to prevent security incidents before they occur. This approach is more flexible and adaptable than traditional privilege control methods, as it can respond to changing circumstances and emerging threats.
Benefits of Intelligent Privilege Control
There are many benefits to implementing intelligent privilege control in your organization. First and foremost, it can help to prevent security incidents before they occur. By detecting potential threats in real time, intelligent privilege control can take action to prevent them from escalating. This can save organizations time and money, as they won’t have to deal with the aftermath of a security breach. In addition, it can help to improve efficiency and productivity. By providing users with the right level of access, they can perform their jobs more effectively and efficiently. Finally, intelligent privilege control can help organizations to comply with regulatory requirements and industry standards.
Implementing Intelligent Privilege Control in Your Organization
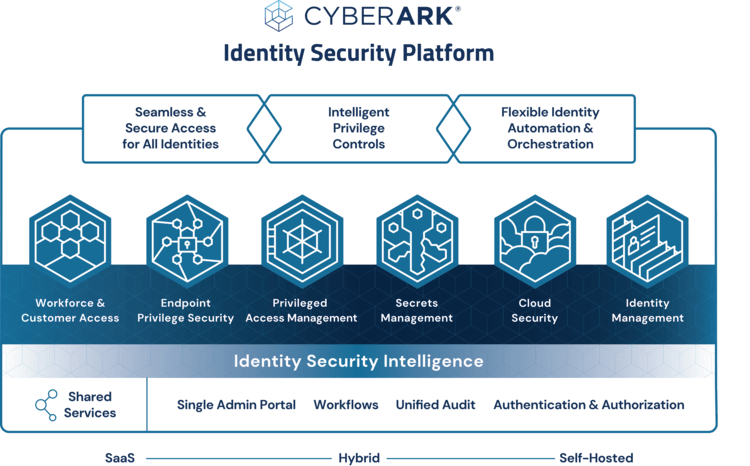
Implementing intelligent privilege control in your organization requires a comprehensive approach. First, you need to assess your current privilege management practices and identify any gaps or inefficiencies. Next, you need to design a new privilege management framework that leverages advanced analytics and machine learning algorithms. This framework should be tailored to your organization’s specific needs and requirements. Finally, you need to deploy and configure the new framework, ensuring that all users are trained on the new system and that it is fully integrated with your existing security infrastructure.
Best Practices for Maintaining Intelligent Privilege Control
Maintaining intelligent privilege control requires ongoing effort and attention. Here are some best practices to keep in mind:
– Regularly review and update your privilege management framework to ensure that it remains effective and up-to-date.
– Monitor user behavior patterns and look for anomalies that may indicate potential security threats.
– Use multi-factor authentication to add an extra layer of security to your systems.
– Implement a strong password policy that requires users to choose complex passwords and change them regularly.
– Provide regular training and awareness programs to educate users about the importance of security and how to protect themselves.

Check out CyberArk’s recently published eBook, “What to Look for in an Identity Security Platform.” It’s a quick read containing vendor-agnostic recommendations on the strategies, controls and technologies that comprise a true identity security platform. In the eBook, you’ll find insights on what questions to ask and how to evaluate providers’ offerings to make sure they can meet your organization’s needs.
Choose AsiaPac as your Intelligent Privilege Control Provider
AsiaPac provides next-generation privilege management, going beyond traditional role-based access control (RBAC) models. Leveraging advanced analytics and machine learning algorithms, AsiaPac’s intelligent privilege control identifies and responds to suspicious activity promptly, mitigating potential security threats effectively.
By choosing AsiaPac as your intelligent Privilege Control Provider, you gain numerous benefits. Their solutions detect and prevent security incidents in real-time, helping mitigate risks and maintain a secure environment. It enhances efficiency and productivity by providing users with the appropriate level of access. Moreover, AsiaPac’s solutions aid organizations in complying with regulatory requirements and industry standards, reducing compliance-related burdens.
Choose AsiaPac as your intelligent Privilege Control Provider to ensure robust identity security for your organization. AsiaPac has earned the CyberArk APJ Best Growth Partner of the Year Award 2022 and the CyberArk Rising Star Partner of the Year Award 2022, highlighting its excellence and commitment to delivering top-notch privilege control solutions.
Conclusion
In today’s digital age, identity security is more important than ever. With the increasing sophistication of cyber threats, it’s crucial to have intelligent privilege control in place. This approach provides a more proactive and dynamic way of managing privileges, as it can adapt to changing circumstances and respond to new threats as they emerge. By implementing this in your organization, you can help to prevent security incidents before they occur, improve efficiency and productivity, and comply with regulatory requirements and industry standards. So, take the necessary steps today to protect your organization’s identity security and ensure a safer digital future.
Tags: CyberArk, Identity Security, Identity Security Intelligence, Identity Security Platform, Identity Security Threats, Intelligent Privilege Control,
Other blog posts you might be interested in:
Trending posts
- Key Advantages of Robotic Process Automation for Your Business Operations
- What is Daas or Device as a Service?
- Empowering Excellence: AsiaPac and the FortiGate Cloud-Native Firewall (CNF)
- Top Reasons Why Admin Tasks Automation Is a Must-Have in 2020
- An SMB Guide: 7 Good Reasons to Backup Office 365
- Dynatrace on AWS: The Eagle Eye Into Your Cloud Environments
